Replacing VPNs with zero trust networks
May 23rd, 2022
|
3 mins 3 secs
|
VPN
Zero-trust
Access control
SETUniversity.com
SET U
The COVID pandemic forced many companies to look for a quick solution to
give all their employees the ability to work remotely. In most cases, that
solution was to use a Virtual Private Network (VPN) security model.
Unfortunately, however, VPNs have several disadvantages. For example, they are
not intended to support cloud infrastructures and are difficult for end-users
to deploy on their own devices.
The pandemic was not the only reason for the popularity of VPNs. This
model has been used for many years by companies to extend the reach of their
corporate networks beyond their physical boundaries, without the need for
expensive dedicated connections. In such situations, the disadvantage of VPNs
is that they generate tunnels that pass through several local networks with
critical resources. And if people with bad intentions manage to get into one of
those tunnels, they will have those critical resources at their disposal.
VPN tunnels are supposed to employ secure protocols to prevent
unauthorized users from hacking into them. But managing those protocols
involves an administrative effort that increases with each new user who needs
access to the network. Thus, VPN administration costs escalate proportionally
with the number of accesses.
Enter the Zero-Trust Model
The zero-trust architecture was created as an alternative to VPNs that
adapts to cloud environments and provides more flexibility than encrypted VPN
tunnels. Most interestingly, its management costs do not scale in proportion to
the number of users.
In a zero-trust security model, authentication is applied to every user,
device, and application, for every attempt to access a resource.
What is zero trust?
The basic principle of zero-trust security is that no one is trusted.
All users and all devices are restricted from accessing the resources available
on the network, regardless of whether they previously had any access to those
resources. And regardless of whether the user or device is inside or outside
the organization.
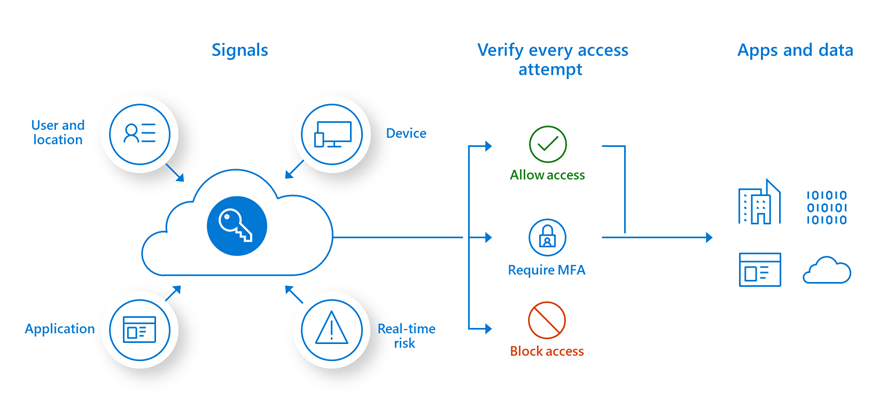
Zero-trust security model in Microsoft 365. Source: Microsoft.
When a user or device attempts to access any resource that is within a
zero-trust network, it must undergo a quick but strict authentication process.
Preferably, a multi-factor authentication (MFA) process paired with
strict access control policies.
Deployment of a Zero-Trust
Network Architecture
Implementing a zero-trust network requires prior work to carefully
define permissions and authorizations, as well as authentication mechanisms.
Even once defined, these mechanisms must be kept up to date. These tasks may
add a little complexity when implementing a zero-trust architecture, but the
complexity and effort required do not increase in proportion to the number of
users. In addition, what is gained in return is a reduction in areas vulnerable
to attack and greater control over access to resources.
Benefits of Zero-Trust
Architecture
In addition to the benefits mentioned above, zero-trust network access
provides a better user experience for remote users, who do not need to go
through complicated procedures to set up VPN tunnels on their personal
computers or devices.
The improved user experience is evident in higher quality video
conferencing and faster application response times. In addition,
resource-specific access management, rather than encrypted tunnels that grant
full access, minimize the risks of lateral movement and ransomware propagation.
In Search of Standards
Although there are several initiatives to define standards for
zero-trust network architectures, none have yet achieved unanimous acceptance
in the industry. However, there are several solutions that seek to position
themselves as leaders in this segment and that could eventually become de-facto
standards, such as
Perimeter 81,
ZScaler Private Access,
CloudFlare Access, and
TwinGate.
These solutions, although they differ from each other, are characterized
by the creation of software-defined security perimeters and seek to automate -
or at least substantially facilitate - the tasks implied in onboarding new
users.
In Closing
The main features to be considered when choosing a zero-trust
architecture solution are; user-friendly monitoring tools, network visibility,
the possibility of controlling on-premises and cloud resources indistinctly,
and compatibility with the main cloud infrastructure providers.



